I've now extended my Drupal on Azure Container App project by integrating SAML 2.0 Single Sign-On (SSO) with Microsoft Entra ID. This was a great exercise in connecting a service provider (Drupal) with an enterprise-grade identity provider (Entra ID).
The core of the project was the metadata "handshake." The Entra ID Enterprise Application required the Entity ID and Reply URL from Drupal's samlauth module. In return, Drupal needed Entra's Login URL, Identifier, and x.509 signing certificate to establish the trust relationship.
An interesting challenge arose when enabling SP-initiated logins. Drupal needed to sign its authentication requests, which required its own certificate and private key. Since the container's file system is ephemeral, I couldn't just generate these files inside the running container.
The solution was to update my Terraform configuration to provision a second, small Azure File Share. I then mounted this new volume to a secure, non-web-accessible path within the container (/etc/ssl/private). This provided a persistent and secure location to store the generated certificate and key, solving the problem while maintaining a clean, infrastructure-as-code approach.
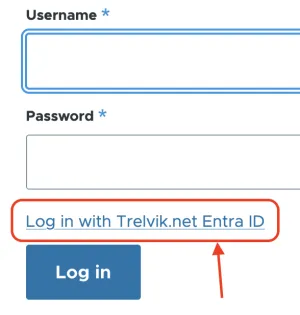
With this final piece in place, both IdP- and SP-initiated SSO flows are now fully functional.
Edit: I've since migrated to a new Drupal install and have decided not to replicate that part of the configuration this time. But it was a good proof of concept getting it to work. Enterprise-grade services ought to always get integrated SSO for both the security and the convenience whenever and wherever they're supported.